APT Threat Analytics – Part 1
January 23, 2014 9 Comments
APT Threat Analytics – Part 1
How can you predict emerging threats? Threat intelligence and analytics continues to dominate the headlines and attention of organizations seeking viable options in their escalating battle against advanced threat actors.
Threat intelligence is evidence-based knowledge, including context, mechanisms, indicators, implications and actionable advice, about an existing or emerging threat to assets. It is used to inform decisions regarding response in terms of prevention enhancements with mitigating controls or detection adjustments (rules or triggers).
This APT Threat Analytics – Part 1 blog discusses best practices to identify internal and external data sources as well as help overcome many operationalization challenges to take an emerging program to the next level as a strategic component.
Value Proposition
The reality of continuously evolving, persistent, sophisticated and targeted attacks is wreaking havoc. Many enterprises only have fragmented or partial security monitoring in place, lacking complete visibility to what is happening in their environments. Detecting this stealthy activity often aimed at specific targets requires the ability to monitor and compare anomalous behavior over time, connecting the dots among multiple events.
The effective use and sharing of actionable threat intelligence has the potential to fundamentally change the way organizations prepare for and respond to attacks. By gathering threat intelligence from various sources and performing risk-based analytics enables mitigating controls to be proactively identified – applied to the APT Detection Framework to assess coverage and gaps – and put into place to provide better protection against emerging threats and vulnerabilities.
Terminology Definition
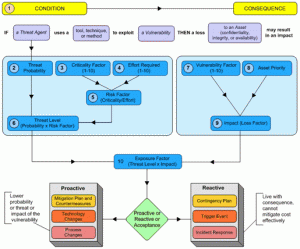
Risk management processes and frameworks are an important component in threat analytics in order to make sense of the feeds and gain actionable and tangible benefit. The importance of these fundamentals will become more clear as we progress through this blog.
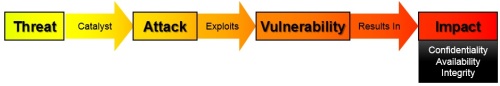
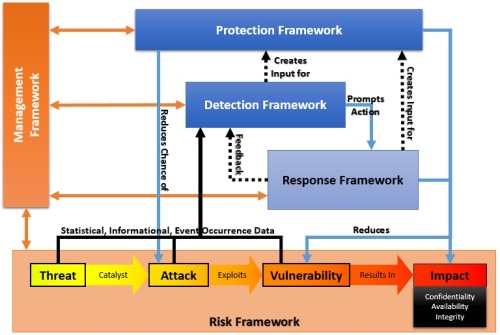
Risk is defined as the likelihood that a particular threat using a specific attack will exploit a particular vulnerability of a system that results in undesirable consequences.
Risk Framework
Risk Management – The process concerned with the identification, measurement, control and minimization of security risks in information systems to a level commensurate with the value of the assets protected.
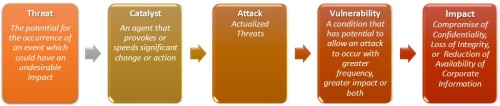
Threats – Threats exist simply as the potential for an event to occur. Attacks occurring to others, but not us, are threats, while threats that have been seen as attacks on us have moved off of the threat phase and into the attack phase.
Catalyst – A catalyst serves as the trigger that causes a threat to be realized as an attack. Business conditions, financial gain and political motivation may all serve as these triggers. A catalyst moves the flow of risk from existing as threat to occurring as an attack.
Attack – Attacks are threats that have become actualized events that may have an adverse impact. Attacks may be intentional or non-intentional and may occur as directed or non-directed.
Vulnerability – Vulnerabilities can allow an attack to: pose as another user or entity, execute commands or access data that is contrary to the specified access restrictions, reduce availability of an asset, or to hide activities. Vulnerabilities may also be considered as a point of entry that an attack may attempt to use to gain access to the system or data.
Back to Basics: Placing Threats in Context
Anything that may increase risk according to security policy, standards or guidelines may also be considered a vulnerability. While vulnerabilities may have many causes, some of the most critical are apathy and ignorance. Lack of awareness of security issues is a common cause of vulnerabilities.
Impact – The final phase of risk is actual impact. Loss of Integrity, Compromise of Confidentiality or Reduction of Availability to any asset has an adverse affect on the business. The implications of a threat becoming an attack that succeeds in causing disclosure, destruction or alteration of business assets range from financial loss to reputation damage.
The interaction of security solutions with risk, once it causes impact, are to reduce the impact, eliminate additional impact and/or institute recovery processes.
Threat Profile
A problem that many companies face is that they don’t fully understand the threats against their organizations. Creating a threat profile is a key step in understanding what threats a company faces and the potential impact if an attack were to be successful. A threat profile can also help companies prioritize resources in order to successfully defend sensitive data.
There are different ways that organizations can create threat profiles, we will cover some examples of applicable risk management frameworks and threat profiles in future blogs. The best option is to use or evolve established risk management processes or frameworks.
Risk Management Methodology Example
Threat profiles based on typical risk management methodology include scenarios about known sources of threats and typical outcomes. This valuable information enables organizations to move from being vulnerability-centric, with no real prioritization or protection of assets, to a more threat-centric posture, including strategies for defense and incident response.
Threat Intelligence Sources
The goal of threat intelligence is to reduce the danger of zero-day malware and other unknown attacks by providing early detection and near-real-time alerts.
There is certainly no shortage of threat intelligence sources and the staggering volume of data can be paralyzing. When it comes to intelligence, less is more. It is much better to have a smaller number of high-value sources than to be inundated with low-value ones.
In APT Threat Analysis – Part 2 we will discuss both the commercial and open source projects. Vendors compete head-to-head with each other on product features, functionality, and usability. The key point is that they should also compete on the overall accuracy, timeliness, and scope of their security intelligence – as well as standard APIs for open security intelligence integration with standardized data formats.
By their very nature, open source solutions are extensible and offer the ability to act on intelligence. Ideally CISOs should become active lobbyists for an open security intelligence market. This could help avoid the coming deluge of security intelligence as the right feeds are selected that align with organizations and to use this intelligence for its intended purposes – to lower risk and accelerate incident detection and response.
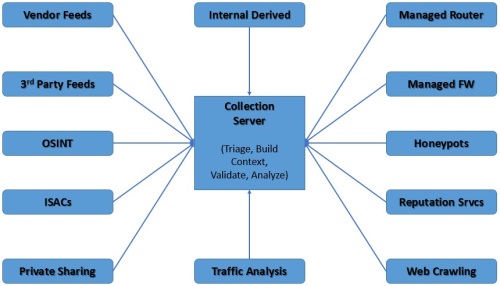
Threat Data Sources – Internal
For many organizations that consume threat intelligence, a key challenge is how to consume and act on that intelligence. Organizations should start small with just a few threat sources, start with a smaller internal prototype to deal with variances in data quality and relevancy and work out the process and kinks to derive useful actionable results then expand externally in iterative steps.
Once an analyst has gone through the intelligence cycle and has a qualified threat indicator, they must be able to apply it to the organizations security controls.
Threat Data Sources - Internal
Threat Data Sources – Global
Security teams need even greater coverage of malicious activity from multiple sources to have a better understanding of what’s going on globally—as opposed to just the network under their control. They are turning to external systems that provide worldwide data correlation and analysis.
Most enterprises don’t have the staff or resources to do their own external threat intelligence gathering, so it makes sense to subscribe to a service that provides prepackaged threat intelligence data. This can be used in conjunction with managed security devices or fed into in-house-based sensors to better understand developing threats.
Threat Data Sources - Global
For those organizations who leverage APT Red Teams then that becomes another invaluable threat source and key validation of the organizations current security posture, to enable continuous improvement and optimization from counter-intuitive sources and help mitigate advanced threats.
The Importance of Analytics
To make threat intelligence usable within your organization, you must rein in all the data and make it scalable. Analysts need a platform that enables the prudent integration of both internal and external intelligence.
Intelligence isn’t all about sources and indicators … it is about analysis
Threat indicators typically include data items like IP addresses, fully qualified domain names, MD5/SHA-1 hashes, SSL certificates, filenames, mutexes, and registry keys. Much of today’s threat intelligence comes in the form of simple indicators. Unfortunately, attacks aren’t simple, and lists of indicators alone don’t always offer value to the organization. Please see APT Detection Indicators for more information on developing and using Indicators of Compromise (IoCs).
From Feeds through Analysis to Governance Actions
Correlation is key to turning all this data into intelligence so that defenses can be updated to address, closing the gaps and window of exposure more quickly. Chaining together multiple events and alerts makes it possible to identify sequences of activity that can equate to a far more severe incident. Correlation also helps validate the severity of threats by lowering the rate of false positives and noise.
Analysts need robust capabilities to query and interact with raw intelligence to determine what the implications to their organization are. The ability to pivot and uncover relationships that would otherwise be obscure is key. Visualization should also be a core capability making analysts’ jobs easier.
Feeds and Feedback
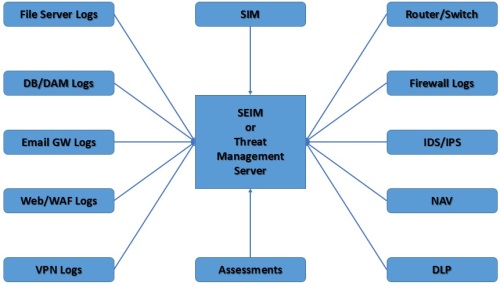
Once the organizations threat profile has been created (from above) and consumers of the threat feeds have been identified, the data has to get to the right places so it can be acted on. It is easiest to get this information to the security operations group because the majority of threat intelligence data will go directly into the SIEM.
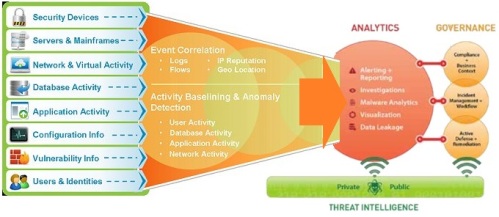
Information Security Management Ecosystem
An important, and sometimes overlooked, step in the threat intelligence consumption process is providing feedback on the relevance of the data received and the effectiveness of action taken.
Conclusion
The rise of threat intelligence services is helping enterprises gain more insight and visibility into global and industry-specific threats. But organizations have to figure out how to take that information, make it actionable and put it in the right hands so it gets implemented in a timely manner.
The key feature of leveraging threat intelligence with analytics is that it produces predictive threat warnings and mitigation advice by monitoring security events from a wide and diverse variety of sources. Using heuristics and correlation techniques to analyze millions of global events, organizations look to uncover malicious activities.
Instead of using traditional signature-based analysis at the network perimeter, the Threat Management (or SEIM) platforms use IP, URL and file reputation services; contextual analysis; and behavioral rule sets to uncover and block access to malicious content, with some even adjusting or changing their security strategies in real time.
The big advantage is that, done right they consolidate threat, vulnerability, risk, fraud, spam, phishing, attacker and network intelligence information, overcoming the problem of information being fragmented and disparate stored in silos.
Coming Soon
In APT Threat Analytics – Part 2 we touch upon commercial, government and open source threat intelligence sources. We will focus on interesting emerging standards, such as Structured Threat Information Expression (STIX) as well as Trusted Automated Exchange of Indicator Information (TAXII) which are beginning to be embraced by startups such as Confer.
For open source, Bro Network Security Monitor, OSSIM, Snort, and YARA are just a few examples of projects that enable you to share threat intelligence across your ecosystem. The Security Onion packages many open source projects into a Linux distribution (for more information see APT Detection Indicators).
In future parts we will also delve further into the process of reviewing external feed sources (pros and cons), triage, building context, validation of data, and performing analysis as well as discuss the development of organization threat profiles based on risk management process.
References
This APT Threat Analytics – Part 1 blog is also a part of the APT Strategy Series and Security Architecture Series. For a complete listing of all NigeSecurityGuy blogs see the Security Series Master Index.
Thanks for your interest!
Nige the Security Guy.


Pingback: APT Strategy Series | Nige the Security Guy
Pingback: Security Series Master Index | Nige the Security Guy
Pingback: Page not found | Nige the Security Guy
Pingback: Defensible Security Posture – Part 2 | Nige the Security Guy
I would review the definition of Vulnerability, to introduce the terms Weakness and Exposure.
I would also have more feedbacks regarding the terminology if you’re open for it.
Are you familiar with the NIST Risk Management Framework (RMF)?
Thanks and keep it up, very interesting
Thanks. I am very open to any feedback and comments.
I will add some further definition to vulnerability and link to the Threat and Vulnerability Management blog where I intro CWE and CVE. I may do another blog to go into greater detail in this area and the importance of risk management life cycle generally.
There are a few risk frameworks but the key is to keep it practical and meaningful to identify and manage critical assets.
It is more important to have a process and then evolve it than buy into vendor hype and buy a theoretical silver bullet.
Thanks for sharing. Look forward to hearing from you.
Nige.
Pingback: Security Strategy Retrospective | Nige the Security Guy
Pingback: APT Threat Analytics – Part 2 | Nige the Security Guy
Pingback: APT Strategy Guide | Nige the Security Guy