APT Detection Framework
November 12, 2013 29 Comments
APT Detection Framework
APT Detection Framework – Part 2
The last decade has seen a lot of research on intrusion detection with intelligent data analysis and its implementation in commercial products but there are still some challenges remaining. Effectiveness, accuracy and scalability are key considerations in the technical design, implementation, and operations of an IDS.
This blog presents a proposed APT Detection Framework that can be used both for advanced multistep threat scenario analysis as well as detection system design – to identify an organizations gaps based on new threats and/or indicators of compromise and make iterative improvements.
The APT Conundrum
Advanced threats and stealthily targeted attacks against organizations are seeing an increase in complexity and persistence. These more complex attacks are aimed at penetrating networks to obtain critical intellectual property and/or sensitive data to be used for financial or competitive gain. The difference with cyber attacks from a couple of years ago is that attackers take more time and effort to remain undetected.
Common intrusion detection methods lack in their ability to detect such complex attacks. They do not correlate individual suspicious events to detect these advanced attacks. A new approach to detection is therefore needed which takes the multistep characteristic of these advanced persistent threats into account.
Intelligent Data Analysis
In order to begin to understand and to be able to defend against targeted attacks a detection matrix is needed for visibility, analysis and, to ensure that all threat scenarios are considered with no gaps in defense. The matrix can be used as a tool to relate attack characteristics with analysis methods and business criteria.
Traditional signature based detection algorithms with correlation engines are still needed but the advanced approach of the attackers requires the additional use of intelligent data, i.e., indicators or triggers that can be correlated for example in a Security Information and Event Management (SIEM) system.
[Our next blogs in the APT Strategy Series will discuss both Indicators of Compromise (IOCs) as well as APT Detection Use Cases in more detail to more fully leverage SIEMs in a SIEM Maturity Model.]
The proposed detection matrix is used as a roadmap to design and evolve a holistic security system capable of detection of advanced persistent threats. Use cases developed from threat scenarios are used to evaluate the resulting system design for gaps and weaknesses. These APT threat scenario use cases illustrate that not all activities of attackers will be detected by current technology alone and that human analysis of indicators produced by the system remains necessary. The proposed framework enables the analysis and consideration of key questions, such as:
- What is the structure of Advanced Persistent Threats?
- What indicators can be used for detection of APTs?
- What business requirements, policy, assets influence the detection system design?
- What design choices lead to a detection system which can detect APTs?
- To what extent can the system design detect APTs?
APT Detection Framework
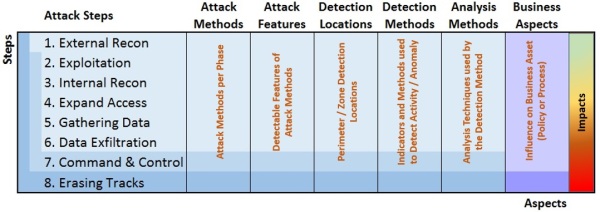
The proposed APT Detection Framework maps the high level attack structure of multistep attacks and low level attack methods to the design of detection systems, both automated technology as well as additional tools and techniques. The proposed framework is constructed as a matrix in which the rows are used to represent the different attack steps and the columns represent the different components related to attacks and detection.
The proposed framework is shown below.
APT Detection Framework Overview
The first column, Attack Steps contains the different phases of an APT which can be identified, it also shows the overlap amongst the steps containing activities which are distinct in nature but are executed at the same time. For example, Command and Control actually covers steps 2 through 7 (see vertical blue line on left) and there are others that execute in parallel to other steps, not strictly sequentially depending upon the APT signature. The presented framework has eight steps, but this might differ per specific attack signature or due to changes in attacks over time.
Attack Methods lists the various methods which are known to be used within the steps. Attack Features goes into more detail, it is used to identify and describe detectable indicators or triggers. The Detection Locations where these attacks and aspects can be detected and/or contained by a control point are listed in the fourth column.
The next column, Analysis Methods links the previous columns to common detection methods. The column contains a description of analysis methods used by the detection methods in the previous columns.
The last two columns contain categories which are not part of an attack per se but do influence choices on defenses against them. The Business Aspects are influenced by the possible impact of an APT or the occurrence of one of its steps. The cost of an APT occurring should be considered as a guideline as well as if this is a capability that the organization should build and operate with skilled resources, something that is co-sourced in a partnership or outsourced as a managed service.
The accuracy of a detection system is the most important aspect from a business perspective. A noisy system with too many false positives has a higher operational cost but a system that misses attacks does not prevent losses. Cost/Benefit analysis shows that systems that use multiple methods are considered better from a cost perspective.
Use of the Detection Framework
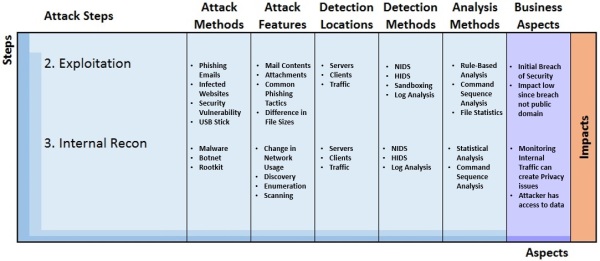
The APT Detection Framework can be used in different ways. It can be used for analysis of attack scenarios ranging from detailed to general analysis. The figure below illustrates two oversimplified steps as an example use case attack in the model at a high level.
APT Detection Framework Example
In APT Detection Framework – Part 2 we will provide our readers a more detailed set of examples together with more description on each of the APT Detection Framework matrix cells.
APT Detection System Design
Another way of using the framework is to use it as a roadmap for development of a more comprehensive and evolving detection system. The attack analysis is input for design choices of the system and ultimately the choice of analysis methods. This can be used to identify indicators and/or trigger combinations that are then combined together in a SIEM to correlate and alert on the combination for further investigation into potential suspicious activity.
APT Detection System Design
The first column gives the attack steps and with that the structure of the APT. The second column with attack methods indicates real methods like denial of service attacks or malware related to botnets. Components like attacked ports or control messages are general aspects of these attacks that can be used for detection. These are the features which can be used for detection. The location column forms a link between the attack and the detection methods. The choice of location limits the available attack features for detection. The detection method column contains detection technology like virus-scanners, firewalls, honeypots and traffic capturing equipment, currently in use for detection.
Conclusion
APTs are a complex attack scenario in which different low-level attack methods are used in a multistep approach to achieve a predetermined goal. They are executed with more stealth than normal attacks. This is often achieved by specifically targeting employees or by using zero day exploits. This stealthy approach makes it harder to detect APTs with standard defenses like firewalls and virus scanners. An approach for detection of APTs should be aimed at detecting different elements of attack scenarios. The framework presented in this blog can help analyze APT threat scenarios with the purpose of creating a means of detection of APTs.
Effectiveness, accuracy and scalability are key considerations in the technical design, implementation and, operations of an IDS. The application of this detection matrix provides a good approach for attack analysis and detection design aspects. Intelligent data analysis methods are shown to improve detection as another layer in the APT Defense-in-Depth Toolkit but still does not replace other technologies such as signature and anomaly detection.
References
This APT Detection Framework blog is a part of the APT Strategy Series and complements and builds upon the Defensible Security Posture and Adaptive Zone Defense blogs.
In APT Detection Framework – Part 2 we will build upon this foundational introduction with some practical use cases and examples and begin to tie together with APT Detection Indicators.
For further information this blog was based upon the research paper, “Towards a roadmap for development of intelligent data analysis based cyber attack detection systems” written by J.A. Vries dated July 5, 2012.
Thanks for your interest!
Nige the Security Guy.