Architecture Case Study – Part 2
July 16, 2013 5 Comments
Architecture Case Study – Part 2
Architecture Case Study – Part 1
The Security Architecture Series shares the steps involved in requirements gathering, baseline, product and solution selection and, through to realizing the architecture. This blog continues an Architecture Realization Case Study that uses those principles and recommendations as a practical example.
The use case study clearly demonstrates that a focus on the details, i.e., detailed preparation and planning enables and ensures a smooth and successful implementation and migration.
In Part 1 the blog took readers through the highly collaborative use case program to develop an Architecture, identify requirements in an RFI, map responses and short-list vendor solutions and, conduct a network security evaluation to select contrasting best-of-breed versus integrated solutions. The steps presented were, as follows:
- Develop Architecture
- Requirements
- Specify Functional Requirements (RFI)
- Request Information from the vendor community (Distribute RFI)
- Review RFI responses
- Select vendors for product/solution evaluation
- Vendor/Product Selection
- Conduct bake-off testing with business unit participation
- Review evaluation scorecard results
- Conduct pilot of highest ranked solution
- Review pilot results
- Technical Recommendation
In Part 2 this blog discusses the development of the network security design based on the solutions, development of a repeatable deployment program and, the phased implementation and migration across 20+ business units. In this blog we will present, as follows:
- Develop Design
- Develop Implementation Program
- 4 Phases
- Alpha Test
- Beta Test
- Deploy/Execute
- 9 Step Program
Based on the Technical Recommendation developed from part 1 a best-of-breed solution was identified sourced from a single vendor that closely mapped to the RFI requirements as well as tested the best in all 4 categories, Firewall, IPS, VPN and, Management. The selected solution was deployed in the business unit simulation lab as a proof of concept to further validate and for practical hands-on study as a basis to inform the design phase.
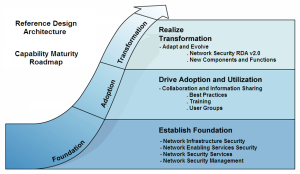
Baseline Network Standard Design
For the Design phase the program team re-convened the Network Security Working Group to work together to develop the design, the same technique that was employed for the Architecture and RFI.
The Design was already defined at a conceptual level by the Architecture and the Functional Requirements (RFI) added a lot of bounding detail. In this phase we wanted to define those further in a more detailed design as well as fully leverage the functionality and capability of the selected solutions while being cognizant of any constraints or caveats.
Our goal was to establish a practical and sensible baseline design, to develop something that could be deployed across all 20+ business units easily and then evolved over time once the prototype foundation was in place. We did not want to make things too complicated, keep things simple and roll-out the solutions, migrate and then seek to evolve in discrete phases of capability maturity.
The team developed the Baseline Network Standard Design while using the lab both as a proof-of-concept as well as validate the design and finalize it per the approval processes used for the Architecture.
Deployment Program Development
The major goal for the development of the deployment program was that it needed to be programmatic and repeatable since the solution components, i.e., Firewall, VPN, IPS, Management were being deployed to 20+ business units with various current technologies and maturity. The steps for this process were identified, as follows:
- Draft Stage
- developed the initial framework with a technical approach, proof of concept, initial templates and tools, and dry run
- Alpha Stage
- partnered with an alpha business unit to initially validate the technical design, deployment approach, templates and tools
- Development Stage
- fully developed and baked the Reference Guides, Templates, Tools, Bill of Materials (BOM) template and, Kick-Off presentation
- Beta Stage
- partnered with two business units to more precisely verify the deployment program to work out any glitches and ensure repeatability
- Deployment Stage (Production)
- program developers hand-off to 3 deployment teams and fallback to a tier support, to monitor and refine the process
- deployment teams partnered with early adopter business units and rolled out to 20+ business unit in schedule
 The technical deployment aspects of the program were complemented with a plan that both provided a breakdown of the 4 solution components (Firewall, VPN, IPS, Management) into a phased deployment, as illustrated below.
The technical deployment aspects of the program were complemented with a plan that both provided a breakdown of the 4 solution components (Firewall, VPN, IPS, Management) into a phased deployment, as illustrated below.
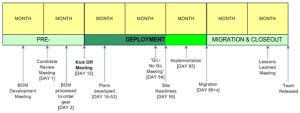
Each Phase was then further defined to describe the timeline with pre-deployment planning, official project kick-off, deployment and then migration and closeout, as illustrated below.
Once the Alpha and Beta stages were completed and any lessons learned factored into the program the team worked with the business units to identify the flow of deployments based on candidate selection criteria and develop a program deployment schedule using 3 deployment teams.
Phased Deployment and Migration
Once the technical and process components of the deployment program were developed they were validated and tested with the above methodology, through Alpha, Beta, Early Adopters and, Rollout. Each step built upon the other, both validating and refining the technical design and process towards the ‘production’ rollout with the 3 deployment teams. Deployment consisted of 4 high-level categories with 9 discrete and repeatable tasks, as follows:
Kick-Off (Initiation)
In this phase the deployment teams engaged with the business unit to perform Discovery, to gather data to profile the business unit in terms of current state, business requirements, and so on as input into the design task. A formal kick-off meeting was also held to present the project to stakeholders, address any questions and, discuss/validate the project plan timeline.
Planning
In this phase the detailed design was developed using the program Design Reference Guide to populate the business unit template to capture custom options, specifics of the network architecture and, the detailed configuration. The business unit design was reviewed and approved.
The Approved Equipment List was used to identify and size the components required (Firewalls, VPN, IPS, Management) for the target business unit in order to develop the Bill of Materials (BOM) and place the order for devices to be ready for staging and then deployment.
Based upon the design preparation planning was performed to discuss and document the logistics and maintenance windows for the Execution phase. There were two deployment maintenance windows scheduled to provide a backup in case an unforeseen problem occurred. The second window was never needed since the key to success was focused and thorough preparation and planning which enabled successful and flawless execution. A lot of contingency was built into the program.
Execution
In this phase the team split the tasks into 4 discrete tracks with Site Readiness, Implementation, Migration and Decommission. These were split into parallel tracks with a different focus.
Site Readiness was focused on the Network Infrastructure Layer. The team had designed a Transition Zone which enabled the new components to be deployed and tested without affecting the production network. It also enabled the rapid seamless cutover to the new environment for validation and, fallback if/when needed. This task focuses on the technical logistical preparation and configuration.
Implementation was focused on the Network Security Layer, validating the new components in terms of their base functionality as well as integration into network services, such as authentication, logging, network management, and so on. It also performed functional testing to ensure that the environment was operating correctly in terms of stateful failover, remote access, and so on.
Migration was focused on the Application Layer, translation and conversion of existing policy and rules (ACLs, Firewall rules) to the new solution. There were two options, either expedited where all new rules would be applied and tested at once or incremental depending upon business unit size and/or complexity. A comprehensive application testing plan was used to ensure that during cutover all key applications and communications were operating correctly and there were no issues.
Training
During the project initiation training was provided on the technology solutions, in-scope functionality, technical design, future direction, operational best-practices and, network security management using the lab. The business unit stakeholders were a part of the project team intimately involved in the design, implementation, migration and, cutover to make them as hands-on as possible and capable to take a transition.
Closeout
Once the deployment was complete a project closeout meeting was held to ensure that the business unit was comfortable with the operations and that the training program and knowledge sharing had addressed the ability and comfort for ongoing operations and support. The project was closed out and deployment team backed out to provide tier support and subject matter expertise (SME) as needed.
Conclusion
This Architecture Case Study can be seen as a Cadillac use case where it is atypically a fairly large organization with 20+ business units that has the resources, time and, budget to develop a comprehensive and repeatable program that crosses all t’s and dots all i’s. However it is shared with readers as an example from which specific best-practices and/or subsets of the program can be successfully leveraged by any organization to either improve or add to their current deployment or migration processes. Further details are available upon request.
Think You’re Secure? Think Again.
Security Architecture Primer
Security Architecture Baseline
Risk-Aware Security Architecture
Develop Security Architecture
Product and Solution Selection
Security Architecture Implementation
Adaptive Security Lifecycle
Thanks for your interest!
Nige the Security Guy.