Security Program Best-Practices
June 14, 2013 7 Comments
Security Program Best-Practices – Part 1
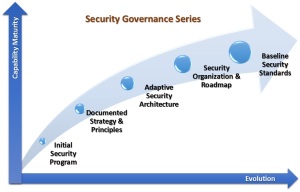
Security Program Best-Practices – Part 2 Part 3 Part 4 Part 5This ‘Back to Basics’ blog series highlights some foundational best-practices and recommendations – as part of the capability maturity model – to enable evolution towards an ever improving more comprehensive and proactive cyber security governance and management program. These recommendations are drawn from a broad sample of assessments where these are typical gaps, deficiencies or need for improvements.
The Opportunity Matrix
The diagram below presents an Opportunity Matrix, a series of articulated next step opportunities for organization’s to build an adaptive, holistic, integrated and, proactive Security Program that enables an iterative process improvement evolution towards a common sanctioned goal. They are graphically illustrated across three dimensions in terms of, as follows:
- Impact and Benefit
- Initiative and Effort
- Relative Cost Estimate
The Opportunity Matrix can be used as a tool to reflect the above parameters as an aid for both planning as part of the Adaptive Security Lifecycle methodology as well as to seek support, budget and resources from executive management.
These opportunities are considered as ‘low hanging fruit’ best-practice initiatives and are listed for brevity as ‘gaps’ that organizations can progressively develop and evolve in a capability maturity model, based on available budget, resources, and priorities.
- GAP 01 – Identify Requirements: Security Policy, Regulation and, Laws
- GAP 02 – Develop Security Governance Program
- GAP 03 – Establish Network Security Organization
- GAP 04 – Establish Security Collaboration Working Group (WG)
- GAP 05 – Develop and Maintain Network Security Standards
- GAP 06 – Develop Network Security Architecture (3-5 Year Objective)
- GAP 07 – Develop Network Security Roadmap (with Annual Plans)
- GAP 08 – Integrate Central Security Logging
- GAP 09 – Establish Network Security Management & Operations
- GAP 10 – Develop Firewall Rule Lifecycle Management
Gap 1: Identify Requirements
Business Problem
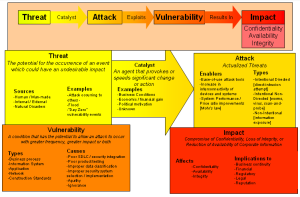
Information security is a business issue, not just a technology issue. Information should be protected for sound business purposes. Corporate knowledge and data are arguably the most important assets of any organization.
Security Policies provide several benefits. They provide a standard baseline of security policy modules and checks, based on the organization’s information security policies and standards. They establish a solid, scale-able basis for an enterprise-wide deployment. Policies heighten security awareness of company personnel. They also help organizations demonstrate their commitment to protecting their vital information assets.
Security policy is not static. It should be a living document and process, which is enforced, implemented, and updated to reflect the latest changes in the enterprise infrastructure and service requirements. It evolves to guard against perceived threats and changing system architectures. A properly designed and implemented security policy is an absolute requirement for all types of enterprises and has to be owned by one group.
The security policy must clearly identify the resources in the enterprise that are at risk and resulting threat mitigation methodologies. It should define which users or classes of users have access to which resources. The policy must define the use of audit trails and verification to help identify and discover violations and the appropriate responses.
Common Compliance Framework
Policies, procedures and standards must be formally documented and reviewed with employees. Without documenting, communicating, enforcing, and raising awareness of corporate standards, security and process improvement efforts will not achieve the intended goals. If employees are not aware of how to properly execute their duties and responsibilities according to these standards, they will be ineffective.
If at all possible take the time to craft a Common Compliance Framework that includes any targeted standards (such as COBIT, ISO 27002, NIST, etc.), all applicable regulations (such PCI DSS, HIPAA, SOX, etc.) and, needed security policy for the business. All too often organizations struggle to assess compliance in silos which increases complexity and proves costly but also there are overlaps and synergies. Many groups offer mapping matrices between various standards and regulations making it possible to combine them as needed. We will cover the Common Compliance Framework in more detail in a future blog.
When developing policies and procedures, document only what can realistically be done. This can be accomplished by involving the process owners in the generation and maintenance of the policies and procedures. Moreover, there must be triggers in the system development life cycle and change management processes to ensure that policies and procedures are updated as the computing environment and risk environment changes. At a minimum, they should be reviewed annually.
Policy Management
Closed-loop policy management is implemented using the network security architecture, and includes configuration management of network devices, enforcement of policies in the network, and verification of network functionality via audit trails. Verification and audit trails close the loop on policy management, and result in updates to the policy to reflect corrective actions.
Gap 2: Security Governance Program
Business Problem
Contrary to some beliefs, companies cannot eliminate all risks for two reasons. First, the internal and external threats that create risk are very dynamic. Second, control investments eventually result in diminishing returns. Instead of focusing time and resources on eliminating risk, a realistic goal should be to reduce risk via Risk Management to a level that is acceptable to senior management and the board.
Benefits of Managing Risk, Compliance and, Audits
Proactive risk management is a process that must be embedded in the organization’s culture to reap significant benefits. It can be used to constantly “tune” the control environment to ensure that correct controls are present and mitigating risks. Without using risk data input, the organization may have the wrong controls—or no controls—in place, which could leave the organization exposed to significant threats, material findings, and excessive costs.
Information technology personnel and resources play an integral risk management role, aiding in threat prevention, detection, and reconciliation. With the help of technology resources, business units and senior managers can work to execute a cost-effective program that continuously identifies, prioritizes, and manages risks.
When designing controls to proactively mitigate risks, consideration must be given to using tiers of controls in the same manner that a castle builder uses multiple walls to protect a fortress. Security personnel call this approach “defense in depth,” wherein layers of controls are used to protect against known and unknown threats that can originate from inside or outside of the organization. Controls must be risk-based and validated.
In some cases, the use of several relatively inexpensive and simple controls may generate more reliable outcomes than one expensive or complicated control. Layered controls also create a “safety net,” in the event that a previous control layer fails. The objective is to have sufficient capabilities to reduce risks to an acceptable level. When auditors review controls and determine that there has been a failure, they will look for compensating controls to offset the level of deficiency. In other words, if one layer fails, they will look to see if any other controls are present to detect or reduce the impact of the failure of the first level. If other controls are in place, the auditor can use his or her judgment to reduce the severity of the noted deficiency.
Continuous and proactive risk assessments and risk management is quickly becoming the norm. Auditing is management’s tool to make sure the entire organization has the resources, systems, and processes for delivering efficient, effective, and secure operations. Audits also are designed to identify key goals, issues, and challenges facing an organization and evaluate its progress against important initiatives. In leading organizations, internal auditors provide independent assurance to key stakeholders while identifying any areas for improvement that management should consider.
For each organization there are different goals and objectives, and certainly different issues and challenges. Therefore, there is no one-size-fits-all audit process, nor one audit approach that fits all situations. There are, however, some common and strategic audit-focused questions that must be addressed in most organizations:
- Is the organization addressing regulatory compliance requirements adequately?
- Is the organization investing in operational excellence?
- Has continuous improvement been studied for applicability and implemented in some form in your IT function? In your various business units? In audit?
- Does governance and risk management practices reflect today’s operating climate?
- Is performance meeting the needs of your users and partners?
- Is management forward looking? Or are they just investing in solving current and past problems?
Compliance ensures that an organization’s governance processes are effective and its primary risks are being managed. Compliance is founded on effective controls— those structures, activities, processes, and systems that help management effectively mitigate risk.
A dedicated, independent, and effective internal audit brings a systematic, disciplined approach
to assessing the effectiveness of internal controls and risk management processes.
Because internal auditors are experts in understanding organizational risks and the internal controls available to mitigate these risks, they assist management in understanding these topics and provide recommendations for improvements. At the same time, data gathered from an audit can also help an organization improve its operations across the enterprise.
Tying it all Together
In general, a proactive technology function, compliance function, and management team will study and learn the strategic direction of the organization and implement plans to meet the long-term goals of the organization and continually communicate progress toward the stated goals in partnership with the auditors — together with an agreed yet evolving baseline audit standard.
Audit and IT need to work together in lock-step to seek solutions and evolve in concert rather than randomly select controls and make IT look bad since the goal posts continually shift. An effective internal audit activity understands the organization, its culture, operations, and risk profile. This makes audit a valuable resource for management, the board, and its designated audit committee. The objectivity, skills, and knowledge of competent internal auditors can significantly add value to an organization’s internal control, risk management, and governance processes.
Coming Soon
Security Program Best-Practices – Part 2 will continue this Security Governance Series with another set of gaps for discussion and helpful advice on key components.
Security Program Best-Practices 2 Part 3 Part 4Thanks for your interest!
Nige the Security Guy.