ISO 27002 Security Benchmark
May 28, 2013 13 Comments
ISO 27002 Security Benchmark
Information security plays an increasingly crucial role in protecting the assets of an organization. As no single formula can ever guarantee 100% security, there is a need for a set of benchmarks or standards to help ensure an adequate level of security is attained, resources are used efficiently, and the best security practices are adopted. This blog illustrates a basic methodology to perform an ISO 27002 Security Benchmark and how to evolve towards compliance and become increasingly secure = integration with a Capability Maturity Model (CMM).
What are the Benefits?
ISO 27002 provides organizations with the assurance of knowing that they are protecting their information assets using criteria in harmonization with an internationally recognized standard. Benefits are applicable to organizations of all sizes and all security maturity levels, not only large enterprises.
Organizations with superior IT governance have more than 25% higher profits than those with poor governance
given the same strategic objectives. These top performers have custom-designed IT governance for their strategies.
ISO 27002 compliance can provide many benefits:
- Provides a framework for resolving security issues
- Provides policies & procedures in accordance with internationally recognized criteria, structure and methodology
- Enhances client confidence & perception of your organization
- Enhances business partners’ confidence & perception of your organization
- Provides confidence that you have minimized risk in your own security program
- Can be a deciding differentiator in contract negotiations
- Enhances security awareness within an organization
- Assists in the development of best practice
- A defined process for implementation, management, maintenance and ISMS evaluation
- Evaluations conducted by impartial independent and objective assessors using a proven methodology
- A performance yardstick to harmonized criteria resulting in mutual recognition
- Optimized security delivers lower costs: fraud, inefficiency and errors should be reduced
- May reduce insurance premiums
- Compliance advantages for participation in Global business opportunities
Leveraging internationally renowned security standards not only allows organizations to seek a reasonable goal of due-diligence but also enables them to articulate security posture to external partners and customers.
ISO 27000 Standards Family
ISO/IEC 27001, part of the growing ISO/IEC 27000 family of standards, is an Information Security Management System (ISMS) standard published in October 2005 by the International Organization for Standardization (ISO) and the International Electro-technical Commission (IEC). An Information Security Management System is a systematic approach to managing sensitive company information so that it remains secure. It encompasses people, processes and IT systems.
ISO/IEC 27002 is a Code of Practice for Information Security Management standard. It provides best practice recommendations on information security management for use by those responsible for initiating, implementing or maintaining information security management systems (ISMS). The Code of Practice establishes guidelines and general principles for initiating, implementing, maintaining, and improving information security management in an organization.
ISO 27002 Scope
Within the Code of Practice there are a set of security domains, as follows:
- Risk assessment – see blog Risk Assessment and Roadmap
- Security policy – management direction
- Organization of information security – governance of information security
- Asset management – inventory and classification of information assets
- Human resources security – security aspects for employees joining, moving and leaving an organization
- Physical and environmental security – protection of the computer facilities
- Communications and operations management – management of technical security controls in systems and networks
- Access control – restriction of access rights to networks, systems, applications, functions and data
- Information systems acquisition, development and maintenance – building security into applications
- Information security incident management – anticipating and responding appropriately to information security breaches
- Business continuity management – protecting, maintaining and recovering business-critical processes and systems
- Compliance – ensuring conformance with information security policies, standards, laws and regulations
These security domains contain control objectives with hundreds of best-practice information security control measures recommended for organizations to satisfy the control objectives and protect information assets against threats to confidentiality, integrity and availability.
Capability Maturity Model (CMM)
A Capability Maturity Model (CMM) is a model for judging the maturity of the processes of an organization and for identifying the key practices that are required to increase the maturity of these processes. The idea behind a Security CMM is to define areas of a security program that should have policy. procedures, processes and controls associated with them and then to measure the application and effectiveness of the policy. procedures, processes and controls (capability level) in an organization. A more mature organization is defined as one whose processes are better defined, integrated and managed. Such an organization is said to have a higher capability level than a less mature organization.
The Security CMM defines five capability levels:

ISO 27002 Benchmark
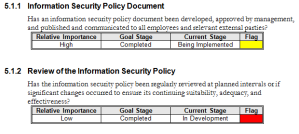
There are many tools and templates available that can help an organization to benchmark their current state towards ISO 27002 compliance. In our case we developed an Excel macro-based tool that factors both ISO 27002 controls as well as maps them to CMM. The user simply makes selections based upon drop-down boxes and adds comments on any observations. See the ISO 27002 Benchmark Visualization Tool sample below:
The tool is used in interactive sessions with IT to discuss the various domains and controls of ISO 27002 and their current state in terms of development, implementation, integration and, maturity. The results are summarized in the checklist as well as the controls are validated to ensure accuracy. Once the exercise has been completed for all sections within ISO 27002 then the macros can be executed. They operate against a default template report in our case to auto-generate the report and enable an efficient and rapid benchmark. The deliverable report is then further developed with placeholder sections to customize and add expertise, industry trends and best-practices to management. An extract of the raw report is shown below.
The tool additionally auto-generates ISO 27002 Security Benchmark Executive Summary slides that further enable presentation and visualization to executive management on current state as well as the organization’s objectives, enabling ongoing justification and support for the cost and resources needed for the security management and improvement program. The following is a sample of a high-level graph that maps compliance to organizational objectives and CMM.
“Security is not a product, it is the ever evolving integration of solutions and process based upon
industry standards, proven methodology and, best practices.” Nigel Willson
ISO 27002 Compliance Lifecycle
Once the organization has performed an initial Baseline Benchmark then the results can be evolved into an on-going lifecycle benchmark process and ISO 27002 compliance measurement program. Performing benchmarks quickly and efficiently reduces the burden and enables timely reporting on progress, depending upon organization’s size that is quarterly, bi-annually or, annually. It can be used to demonstrate progress and trends in what has been achieved and what is left to do. The following is a high-level example ISO 27002 Compliance Lifecycle.
- Baseline Benchmark – Assess the status of security management processes and controls
- Regular Checkpoints – Perform periodic health checks to compare and contrast improvement and compliance progress
- Identify Gap – Use gap analysis to identify the divergence of current state security against the standard goal
- Statement of Applicability (SOA) – Describe the relevance of the standard’s controls to your organization
- Security Improvement Program (SIP) – Develop cyclic process to recommend the measures required to overcome the divergence identified in the gap analysis
Critical Success Factors
Experience has shown that the following factors are often critical to the successful implementation of information security within an organization:
- Information security policy, objectives, and activities that reflect business objectives
- An approach and framework to implementing, maintaining, monitoring, and improving information security that is consistent with the organizational culture
- Visible support and commitment from all levels of management
- A good understanding of information security requirements, through the use of risk assessments, and risk management
- Effective marketing of information security to all managers, employees, and other parties to achieve awareness and ultimately compliance
- Distribution of guidance on information security policy and standards to all managers, employees and other parties
- Provision to fund information security management activities
- Providing appropriate awareness, training, and education
- Establishing an effective information security incident management process
- Implementation of a measurement system used to evaluate performance in information security management and feed back data for improvement.
Conclusion
Management support is necessary at all levels. User awareness programs should also be conducted to ensure that all employees understand the benefits and impacts before the deployment of new security policies and guidelines.
A common problem that crops up after implementation of a standards alignment exercise is an increase in the number of complaints received from users of IT services due to the restrictions imposed by new security controls. The successful implementation of any information security standards or controls must be a balance of security requirements, functional requirements and user requirements.
Although there are a number of information security standards available, an organization can only benefit if those standards are implemented properly. Security is something that all parties should be involved in. Senior management, information security practitioners, IT professionals and users all have a role to play in securing the assets of an organization. The success of information security can only be achieved by full cooperation at all levels of an organization, both inside and outside.
Thanks for your interest!
Nige the Security Guy.