Security Strategy Retrospective
February 12, 2014 Leave a comment
Security Strategy Retrospective
Building a strong foundation, enabling budget and support. For most organizations, justifying an ongoing investment in information security has not been easy. How do you measure the value added to the organization versus something more tangible, like implementing a new business function? What is the vision? What is the risk? What is the plan?
Back to the Future
This Security Strategy Retrospective blog takes readers back to basic principles. It is an interesting reflection on the challenges that security practitioners faced in the mid-90’s which are very familiar and applicable … even today. Organizations are currently concerned about advanced threats with blended multi-step attacks yet many of the practices and solutions from the past are still valid and very helpful as a key security strategy foundation.
The blog takes you on a journey back to the future to tie today’s technology, solutions and requirements to founding well-proven principles. The magazine feature article reproduced in part below was originally published in June 1997 (an extract is presented here). It is quite dated yet discusses persistent behavior patterns and shares key and still valid principles. The more things change the more they stay the same. We have been here before so let us learn from the past.
In future blogs we will take the principles and practices described below to update for a 21st century security strategy and operations framework, in the age of the APT.
Intranet Security: An Investment in the Enterprise (circa 1997)
Simply because data on an Intranet is behind the company Firewall doesn’t mean it’s safe. Here are some issues to consider when securing your Intranet applications.
Creating a Security Strategy
 Organizations are changing the way they do business. The promise of reaching new markets and easily creating new inter-enterprise relationships through Internet technology is sparking unprecedented interest in going online and moving toward electronic commerce. Thus, an organization-wide security strategy becomes vital when business plans extend that same communications model to suppliers, customers, and partners via extended networks. Therefore internal security implemented consistently across the enterprise is fundamental to both the successful evolution of the business and its ability to compete in the global marketplace.
Organizations are changing the way they do business. The promise of reaching new markets and easily creating new inter-enterprise relationships through Internet technology is sparking unprecedented interest in going online and moving toward electronic commerce. Thus, an organization-wide security strategy becomes vital when business plans extend that same communications model to suppliers, customers, and partners via extended networks. Therefore internal security implemented consistently across the enterprise is fundamental to both the successful evolution of the business and its ability to compete in the global marketplace.
So how do you create a secure extended infrastructure? Security is a discipline that’s daily becoming more complex as information systems migrate from mainframes to distributed client-server architectures. As stated above, the extended network adds yet another level of complexity: the need to integrate one more set of technologies into what’s already a complex heterogeneous world.
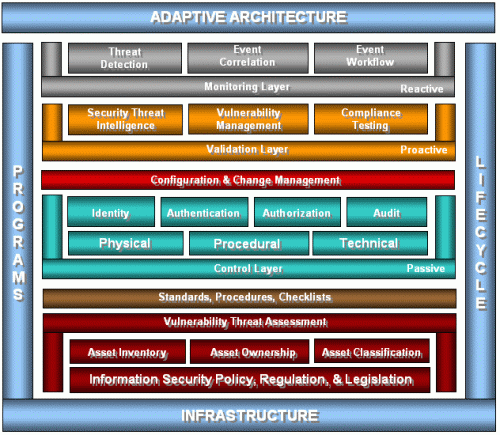
Implemented correctly, the extended network can be the ‘holy grail’ that affords the middleware to hook thin clients to legacy systems, and provides, once and for all, that elusive single sign-on user environment. The illustration below shows a simplified security architecture model that organizations can use as a framework for developing a comprehensive program of organization-wide security.
Security Architecture Framework (circa 1997)
Steps to Success
1. Create a Living Security Policy and Standards. (circa 1997)
The information security policy is the first step in the evolution toward a coherent and cohesive security architecture. Just like a development project, a security policy explicitly defines requirements, and together with strong management, change control and quality process, it provides the framework that bounds security within the organization.
What is security policy and standards?
Security Policy - Procedures, Standards, Process
It’s a set of rules stating what is and is not permitted in a system’s normal operations. Written in general terms, it describes the security requirements that systems must adhere to. Organizations must address a number of policy issues, for example:
- Who is allowed to use the resources?
- What is the proper use of the resources?
- Who is authorized to grant access and approve usage?
- Who has system administration privileges?
- What are the user’s rights and responsibilities?
- How is sensitive information protected?
A security policy and its implementation should be as unobtrusive as possible. If the policy is too restrictive, or improperly explained, it’s likely to be violated. Organizations need to be able to detect and review violations so that they can validate the policy, its effectiveness and appropriateness to address risk and fine tune it – else the policy cannot be used successfully to share requirements and audit.
Security Program Best-Practices: Opportunity Matrix
For more information, see the Security Governance Series: Security Program Best-Practices – Part 1 and onwards (circa 2013).
2. Engage in Information and Resource Asset Classification. (circa 1997)
How much money, inconvenience, and time should be spent to counter an exposure or class of exposure? Taking an inventory of all infrastructure assets facilitates the identification of all potential targets. At the rate some organizations are growing today, it’s no surprise to discover unknown active equipment on an internal network. Finding this equipment and determining ownership establishes responsibility and accountability for what occurs on the equipment.
Classification involves assessing what resources or assets an attacker might want to steal. The inventory forms a clearer picture of exactly which data is critical, and thus which applications and servers need the most protection, monitoring, and auditing. This step lets the organization focus energy – its resources and budget – on the critical and sensitive resources at the optimal level (see below), establishing a priority and minimum required level of protection so those resources can be managed correctly.
The Security Cost Function
By determining which resources need the highest level of protection, you can minimize the cost and the danger involved with putting your data on the net.
3. Maintain an Evolving Security Standard. (circa 1997)
The previous two steps establish a baseline for the enterprise security plan. Together, the security policy and information / resources classification define the minimum standard of security: what to protect and how well to protect it. Because this standard can rarely be implemented within one budget cycle, organizations should develop an annual security program plan as part of the overall strategic roadmap.
Security Program Roadmap
For more information, see Security Architecture Primer, Security Architecture Baseline, and Develop Security Architecture (circa 2013).
4. Conduct Security Audits and Risk Assessments. (circa 1997)
Regular security audits aren’t just for large companies. They’re for organizations of any size that have data to protect from becoming publicly available, to protect confidentiality, integrity and, availability. Security audits should be carried out at least annually, depending upon how quickly the infrastructure evolves and expands. They enable the organization measure its compliance to the security policy and determine the current situation. A risk assessment identifies and quantifies all potential exposures and threats.
At this stage, the consolidation of the current security status with the identification of potential threats allows the definition of security objectives. These objectives are the level of security (protection) the organization has decided on to protect both its own assets and those of organizational units and partners.
In the first year, the security program should schedule the protection of those resources identified as most critical or at risk. In subsequent years, the security plan should document other desired protection measures, as defined in the objectives, and any newly identified critical resources and threats.
In a perfect world, a three year security plan would allow the organization to attain its defined security objectives. However, in reality, any environment continually evolves, and the requirements for protective measures to deal with potential threats need to evolve with it. Implementation of security measures should progress on a sliding scale, ideally in pace with the objectives and threat/risk.
For more information, see Risk Assessment and Roadmap, ISO 27002 Security Benchmark, Security Health Check and, Adaptive Security Lifecycle (circa 2013).
5. Take Security Measures. (circa 1997)
Traditional security is passive and reactive. Extended network security must be aggressive, holistic and proactive. It must be focused on protecting information – the data contents of the system, not the device itself. That paradigm shift changes the rules.
A robust security solution consists of three types of measures:
- Protection measures,
- Monitoring Measures, and
- Validation Measures
An array of monitoring an detection solutions, such as auditing and tracking products, anti-virus software, intrusion-detection schemes, and event logging strategies, can help security managers head off potential security threats before they evolve into serious problems.
Protective Measures
There are three categories of protective measures, they are prevention, detection and, recovery to “Lock the Door“.
A security prevention mechanism applies and enforces security controls during the system’s operation based upon policy, classification and risk to prevent a security violation from occurring. For example, this protection could include a mechanism restricting physical access to a system or the use of logical access control mechanisms based on encryption to prevent unauthorized users from accessing resources. For an update, see Adaptive Zone Defense – Part 1 and APT Threat Analytics – Part 1.
A detection mechanism detects both attempts to violate security, and successful security incidents, when or after they’ve occurred. Alarms can detect unauthorized physical access, and audit trails can detect unusual system activities after they occur. For an update, see Defensible Security Posture, APT Detection Framework and APT Detection Indicators – Part 1.
A recovery mechanism is used after a security violation has been detected, restoring the system to a pre-violation state. Examples include backup tapes and the addition of redundant hardware to a system. For an update, see APT Response Strategy – Part 1.
Validation Measures
Validation measures are proactive. “The lock is checked“. Examples are: active network probing, which involves using commercial and open-source tools to ensure that all unauthorized ports are locked down; compliance testing, using automated processes to validate the exposure to platform specific administration vulnerabilities; and audit reviews, which entail conducting internal reviews to measure compliance to security policy. For an update, see: APT Red Teams – Part 1.
Monitoring Measures
Monitoring measures are reactive: “The security camera detects an intruder“. Examples of these include audit trails, activity monitoring, and policy breach detection.
It’s important to have monitoring and detection solutions that do most of the monitoring work, then send alarms that alert the network security team to threats. In addition, the best-buys in monitoring and detection products are those that can analyze data, rather than just record it. There’s an remerging market for detect and alert technologies that correlate persistent behavior patterns before the damage is done.
For an update, see the upcoming APT Operational Maturity and APT Intelligent Operations blogs.
6. Keep Track of Security Violations. (circa 1997)
A key security function is the centralized logging of application and system accesses. All the security in the world won’t do any good if there’s no way of identifying, investigating, and pinpointing breaches.
In any organization, violations of security policy will inevitably occur. Often, the violation can be classified as caused by an individual’s negligence, an accident or mistake, ignorance of the current policy, or deliberate disregard of the policy. Security vulnerabilities can easily occur as a result of mistakes made by the system administrator introducing weakness, never mind the myriad of patches needed. Obviously, effective audit capabilities must be in place for an organization to fully investigate a violation and determine its classification, what damage has occurred, and what action to take.
But who watches the administrators? Many organizations are tailoring products to audit the administrator, as a hierarchical super-manager overseeing a large distributed base. Network administrators can unwittingly create security holes during routine maintenance and administration duties. The rule of “least privilege” with “separation of duties” is the best practice, where no one person has the keys to the kingdom in all domains, and administration functions, like access control, are shared.
7. Be Prepared. (circa 1997)
The final layer of security is the preparedness to act immediately and correctly when an incident occurs, and to capture and process any perceived threat or incident. This requires the establishment of a reporting process, a response team, and precise well-defined procedures. The need for proper training of staff can’t be over-emphasized, and is a wise investment, saving the organization a great deal of trouble and money in the medium to long term. Tiger teams are very popular ways of honing skills and gaining expertise with security tools. They comprise internal teams of system and network administrators whose purpose it is to test security monitoring and protection measures.
For more information see APT Response Strategy and APT Red Teams (circa 2014).
For most IT departments, justifying an ongoing investment in information security has not been easy. How do you measure the value added to the organization versus something more tangible, like implementing a new business process? Companies often view security measures as insurance, and the risks the measures address are often never quantified and, as such, accepted. Thus, security is a low priority item and the first task to suffer in a budget cut.
However, since the advent of Internet technology and extended networks, the return on investment is very clear. A secure extended network is the key to enabling technology that facilitates the ability to exchange goods, services, and information electronically in a stable, well-managed infrastructure. This provides interaction with customers, partners, and employees promoting loyalty and allowing the enterprise to gain a competitive edge.
Coming Soon
In the upcoming APT Operational Maturity and APT Intelligent Operations blogs we will build upon this dated but valid Security Strategy Retrospective foundation with a similar but updated building block layered security model and an evolving maturity scale. We will discuss the need for a continuously evolving next-generation SIEM, risk management processes and, network behavior anomaly detection that enable organizations to take security operations and situational awareness to the next level, depending upon various factors including threat/risk profile.
Thanks for your interest!
Nige the Security Guy.