Security Architecture Implementation
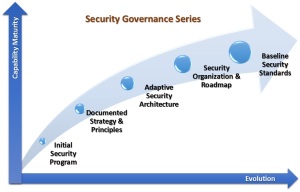
This blog continues the Security Architecture Series by building a Back to Basics foundation before developing upon that foundation with adaptive security in hyper-extended enterprises for a defensible security posture.

The security architecture defines and justifies a number of solution implementation, integration and/or improvement projects each year, based on budget, resources and, priority. As such, a master project plan should be created that takes into account identified dependencies, integration points and any parallel tasks.
To plan implementation of a security solution, you must identify where project execution resources will come from, develop an implementation plan, obtain buy-in for the implementation plan, and create a detailed design for the configuration and deployment of the security infrastructure.
Implementation planning must be viewed as a process first and documents second. In addition, you should keep the technical staff or consultants used during the architectural review on tap to provide implementation planning process oversight. In many projects we have used a Program Technical Architect as the keeper of the vision, direction and, strategy.
Identify Project Resources
First, you must understand and define the scope and resources required for the deployment. These resources include the following:
- Security project manager
- Support functions (administration, contracts, procurement, and others)
- Security engineering development staff (own and vendor’s)
- Security integration team (including part-time contributors and other support organizations within your environment)
- Network operations staff
- Ongoing security operations and support staff
Unless you have a particularly strong and deep security development team on staff, many organizations don’t you will want to make use of vendors professional services. They can, or should, be able to install, configure, and do development work for your product better than anyone else.
However, you’ll also need to have a strong complement of dedicated staff involved with managing and developing the security infrastructure during its early deployment. You also need to have good relationships and well-spelled-out agreements with staff borrowed from other internal functions.
Ultimately, day-to-day operation and support of the security infrastructure will be turned over to an operations organization. However, a security project manager and a few technical support and development resources should remain in place for ongoing integration. You’ll also need staff for pre-production validation, security audit, monitoring, and incident response.
Develop Implementation Plan
The implementation plan should:
- Restate the architecture as a high-level design, plugging in the selected solution components
- Propose a security implementation team (which may be similar or overlapping with the original security architecture team)
- Define an overall project plan and detailed project schedule
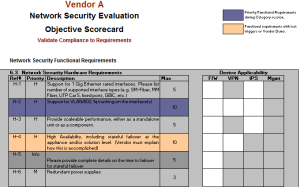
- Identify required resources and other critical success factors, such as a test lab, pilot participants, firewall, or other application configuration changes that must be agreed upon far in advance
- Define project completion and acceptance test plan
- Write an execution-focused risk analysis and mitigation plan
- Develop a communications and training plan
- Compile cost estimates
The architecture, the vendor’s proposal, the high-level design, early project plans, and other working documents prepared during the project must all be consumed, synthesized, and polished to create a realistic implementation plan for going forward (see Security Plan Template). The devil is in the details and time invested upfront in planning and preparation is proven to save lots of time and enable success in implementation and cutover.
However, the high-level design and implementation plan needs to be more than just a piece of paper. Selling the security project is an on-going process.

Implementation planning may well be combined with obtaining the funding and approval to purchase off-the-shelf solution components. It should also be at this point that explicit commitments are obtained to rely on part-time, cross-functional security integration team members. Once obtained, these commitments must be continually reconfirmed; projects fail for lack of stakeholder commitments to do their part for interconnection or configuration.
Obtaining Buy-In and Support
An implementation plans success also depends on the vendor(s). Vendors will provide resources for some stages of the plan, and vendors will be dependent on some of the plans customer-provided deliverables, such as a test lab. The full plan requires a successful triumvirate of dedicated security staff, vendor staff, and the staff of the cross-functional resources that will be integrated or consolidated in this initial implementation.
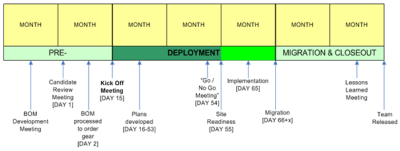
Think of an implementation plan as a process as much as a document. Your security implementation and deployment will depend on the efforts of many people, and they must be engaged in and buy into both the planning process and the activities it entails. Anticipate that the vendor(s) will have to make changes to accommodate your needs. Expect some push back from vendors and cross-functional team members.
Develop Detailed Design and Test Plans
At this stage, a security project moves from architecture and high-level design to detailed design. This process must be conducted by the vendor or at least in close collaboration with the vendor. However, you will want to keep your technical staff or consultants on hand to ensure that the design stays true to the architecture.

Detailed design refines each of the security projects physical, logical, integration, access, management, and administration fine points. It identifies deployment details down to the configuration of roles, entitlements, or attribute syntax.
In parallel with developing the detailed design, an enterprise needs to create detailed test plans. Testing should not be done as an afterthought. It should be baked into the design, roll out, and acceptance process.
Operations Cutover
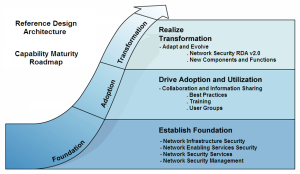
When a key part of the security architecture has been realized, the solutions selected, and the infrastructure implemented and tested, it is time to wrap process around that architecture and transition to the team that will operate and support it. If not, then the architecture and engineering teams will be burdened by the new infrastructure, limiting their ability to move forward strategically. The architecture and security engineering teams will shift their focus to further communicating, developing, and validating the architecture and realizing the next project phase, while at the same time providing tiered support to the operations personnel.

This section enables you to document the all-important processes and procedures for cutover, identify operations roles and responsibilities and don’t forget to conduct user awareness and training to fully complete the deployment.
Document, Document, Document
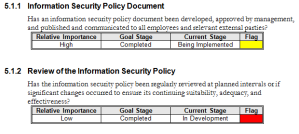
Security support functions fill a vital role within the security of any system. Security standards, procedures, and checklists are recommended as they guide the day-to-day security activities. These processes and procedures should be developed by a knowledgeable person, and be reviewed, documented, formally published, and given to management and staff personnel. The development of procedures helps support a consistent application of the security policy.
Identify Responsibilities and Train Operations
The continuity of service and the high availability of IT services are imperative to the success of operations. Those imperatives will play an increasingly important role in the future. Once a security solution is implemented, there must be someone who is ultimately in charge and who has the responsibility to ensure implementation consistency. The most effective way of ensuring this is through management visibility and support. As such, an effective security management team should be put into place with assurance that they are properly trained.
It may be possible to assign a single individual to manage the overall security of the IT environment and then give personnel with existing responsibilities, additional responsibilities to support security. IT administrators are often very good choices to support, configure, and administer the security of a system/network, owing to their intimate technical knowledge of the operations and services provided. There are also procedures that ensure that the personnel managing the security of the system/network do not overstep their boundaries (i.e., auditing of events and actions taken).
The following high-level items should be considered during this phase:
-
Security Operations and Administration. Operation of a system involves many security activities discussed in this blog. Performing backups, holding training classes, managing cryptographic keys, keeping up with user administration and access privileges, and updating security software are some examples.
- Operational Assurance. Operational assurance examines whether a system is operated according to its current security requirements. This includes both the actions of people who operate or use the system and the functioning of technical controls.
- Audits and Monitoring. To maintain operational assurance, organizations use two basic methods: system audits and monitoring. These terms are used loosely within the computer security community and often overlap. A system audit is a one-time or periodic event to evaluate security. Monitoring refers to an ongoing activity that examines either the system or the users. In general, the more “real-time” an activity is, the more it falls into the category of monitoring.
User Awareness and Training
User training and awareness is critically important to the continued success of any security program. Company insiders either accidentally or intentionally cause approximately 85% of security breaches. Security training instills awareness and enables users to understand the importance of security. In most organizations, security is regarded as required, but not viewed as vital. Most security training material distributed to users is either stuck in a drawer or immediately given away to someone else.

The training program should cover the following “general” types of information:
- Explanation of the security program, its importance, and value
- Who is in charge of the program and specific lines of authority
- Security services, functions, and mechanisms
- Responsibility of the user and management community
- Specific information and information services defined to be sensitive and critical
- The “insider” threat and how to report security incidents
- User and operator errors and how to prevent against these common security problems
- Penalties for security breaches
The most effective way for security training to take root within an organization is for upper-level management to make security an important issue. Once this commitment is made at the higher levels, it will be passed on through the management chain. Migrate from reactive policy, controls and, rules to engage “people” with the skills, knowledge and positive attitude. Empower resources as part of an extended security team to recognize and report potential breaches, issues and/or incidents – provide them the responsibility and accountability to play a role.
Coming Soon!
In future blogs we will cover the Adaptive Security Lifecycle, Identity and Role-Based Access, Application Architecture Taxonomy together with Data Center Trust Zones as key components for the hyper-extended IT enterprise (insourced, co-sourced, managed).
Thanks for your interest!
Nige the Security Guy.