Vulnerability Assessment Remediation
June 13, 2013 3 Comments
Vulnerability Assessment Remediation
The external threat environment has become quieter and much more dangerous. Today’s attacks target specific companies, individuals and data. A typical targeted attack will exploit multiple security weaknesses to achieve the ultimate goal — usually, to steal sensitive data, compromise a specific account or disrupt operations.
Organizations need to present a hardened defensible target to an attacker in addition to the ability to detect and contain. This requires a combination of vulnerability assessment and management processes to find and fix security weaknesses in systems and applications, and the implementation of compensating controls or shielding technologies to protect more legacy systems and applications that will have long-standing vulnerabilities.
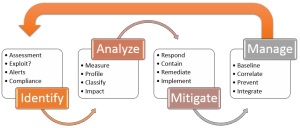
In the Security Assessment Series this blog discusses more tactical and reactive vulnerability assessment and remediation while the next blog in the series will cover strategic and more proactive vulnerability and risk management.
Vulnerability Assessment versus Penetration Tests
Over 25 years I have performed hundreds and hundreds of security assessments for organizations, many of those have been vulnerability assessments and penetration tests. In my experience many organizations seek a penetration test when they really need to perform a vulnerability assessment and address those issues before progressing onto a penetration test. I am often asked to perform a penetration test yet discover the environment is not hardened and suffers from many basic flaws. While a penetration test sounds exciting there are key differences.
A Vulnerability Assessment is designed to allow an organization to identify all of the potential vulnerabilities, validate them, prioritize them based on scores, such as the Common Vulnerability Scoring System (CVSS) for all CVE vulnerabilities (provided by the National Vulnerability Database) and, create a prioritized list for remediation. The scope is broad across many external and/or internal systems. Root cause analysis may be warranted to understand why the vulnerabilities exist and what processes need addressing to resolve fully. These are more tool-based tasks and seek to identify as many potential issues as possible.
Vulnerability assessments typically follow these general steps:
- Catalog assets and resources in a system
- Assign value and importance to the resources
- Identify vulnerabilities or potential threats
- Mitigate or eliminate most serious vulnerabilities
A Penetration Test is either focused on a hardened and locked down environment or a specific platform or service that an organization wants validation to ensure nothing was missed or if there is a yet un-discovered flaw or vulnerability. They are often used as a pre-production validation for sensitive systems or to assess what can be achieved with a mix of advanced threats and social engineering. These leverage more manual methods and will report out on the path the attacker took and the creative exploits used to ‘capture the flag’.
Penetration tests typically follow these steps:
- Determination of scope and target(s)
- Information gathering or reconnaissance
- Exploitation attempts for access and escalation
- Sensitive data collection and ex-filtration testing
- Clean up, evidence collection and reporting
As part of an emerging and evolving network security program organizations should deploy a vulnerability assessment and phased remediation strategy that makes practical sense to address the current and tactical vulnerability landscape and, in parallel evolve that towards a more comprehensive and proactive vulnerability and risk management strategy.
Vulnerability Landscape
During a vulnerability assessment it is possible to discover many vulnerabilities and the sheer volume of data can quickly become overwhelming. This blog proposes a practical and simplified process to get you started, focused on asset inventory and classification to profile the vulnerabilities and thus enable the appropriate prioritization and scheduling of remediation actions.
Taking a complete inventory of the basic makeup of the organization’s network is a critical first step. The second thing is to actually inventory all the mission critical and/or enterprise applications being used. I typically recommend that an Asset Inventory is developed that contains a list of all of the approved assets, services, interfaces, connections and, so on. While this may not be possible in all cases it is extremely important for external accessible services as well as mission critical or core services. This will be covered more fully in a future blog on Application Architecture Taxonomy.
- Inventory –
- Inventory Network Infrastructure
- Inventory Applications and Services
- Identify Device Roles/Groups
- Service Dependency Mapping
- Organization Function
- Service Group
- Applications
- Ports
- Relationships
Classification Asset classification, based on criticality and sensitivity enables the determination and priority of the application of security configuration standards and remediation actions. For example, assets that are in production should conform to all of the applicable security standards as part of deployment and maintenance and critical and/or sensitive assets are prioritized. A future blog will take a deep-dive into data classification.
- Classification –
- Category –
- R&D
- Staging
- Production
- Mission Critical
- Classification –
- Restricted
- Trusted
- Internal
- Public
- Category –
Identification
Ideally, the identification phase should occur during the architecture and design phase (e.g., via security sign-off criteria), immediately prior to the equipment becoming operational (e.g., as a step in the release management process), and at regular intervals throughout the operational life of the infrastructure. Identification and, to some extent, assessment come from activities such as vulnerability scanning and penetration testing – of which this blog provides a foundation and an opportunity to develop a practical methodology and process.
Assessment
Assessment requires knowledge of the technical implications of the weakness, and also of the business implications of the exploitation of the weakness. The risk owner must then make a decision regarding acceptance of the risk, remedial action to fix the weakness or transformation of the risk into another form.
- Assessment –
- Evaluate Vulnerability Risk
- Accept
- Avoid
- Mitigate
- Transfer
- Evaluate Vulnerability Risk
It is a normal practice to rationalize a set of reported vulnerabilities into groups that are accepted but documented, those that have mitigating controls and, those that are mitigated with a solution.
Remediation
Remediation may range from detailed bottom-up technical measures, such as the application of patches, or changes to the configuration of firewalls or other network-based vulnerability protection infrastructure, through changes to custom-made applications, right up to very high-level measures, such as changes to governing policy, processes and procedures or configuration standards.
- Remediation –
- Create Remediation Task Map
- Action Plan:
- Budget
- Resources
- Priority
- Timing
- Immediate
- 30 Days
- 6 Months
- Future
- Typical Actions:
- Patch
- Upgrade
- Configuration Standards Rollout [by Role]
- Infrastructure Refresh
- New Deployment
- Action Plan:
- Create Remediation Task Map
Reporting
Reporting metrics should include frequency of identification exercises (e.g., regular vulnerability reports), and results from identification and assessment, including the number of issues and accumulated risks, and the tracking of remediation actions. In a future blog we will expand this to include the use of a risk register and tracking in the Risk Management blog to report upwards to executive management.
- Reporting –
- Metrics and Trends:
- Number of issues
- Accumulated risks
- Tracking remediation actions
- Metrics and Trends:
The next blog in the Security Assessment Series will develop this theme further to cover more proactive Vulnerability Management Strategy. Once the organization becomes more secure it can evolve to stay more secure.
Thanks for your interest!
Nige the Security Guy.