Adaptive Zone Defense – Part 1
November 15, 2013 21 Comments
Adaptive Zone Defense – Part 1
Adaptive Zone Defense – Part 2
Adaptive Zone Defense – Part 3
Adaptive Zone Defense – Part 4
Limiting and intelligently managing communications between services and systems on an organizations network helps contain an infection or compromise to keep malware or a persistent threat from running rampant. In addition, business needs, regulations and other compliance requirements impact security architecture and design and thus may impose mandated separation or additional boundary controls.
This blog offers guidance to organizations seeking to develop a modular and scalable network segmentation design. The blog is a part of both the Security Architecture Series as well as the APT Strategy Series with the overall goal to improve security around protecting users, applications and access to data to enable a Defensible Security Posture.
Organize for Future Growth
There are dramatic technology changes that are driving today’s network security trends –
- Mobile networks, VPNs and roaming users
- Connect-from-anywhere road warriors test boundaries
- Targeted attacks and APTs
- Advanced Persistent Threats are next generation attacks
- Consumerization and BYOD
- Consumer devices are moving onto the corporate network
- Web application and web server protection
- Attacks on web applications to extract data are more prevalent
- The Elastic Network
- The perimeter is expanding to include high speed 4G, home offices, roaming users, cloud services, and third parties
Importance of Security Zones
Organizations and their IT environments are constantly changing. For some years, these “hyper-extended” environments have been growing more globalized, virtualized, distributed, and mobile. The resulting significant architectural changes require network security zones to become more modular and dynamic while maintaining a level of organization and proactive management to prevent complexity or fragmentation.
Network security zones that separate systems based on their communication and protection needs minimize security risks while allowing information flows to continue even in the face of failures and security incidents. This blog series helps organizations determine how to group IT resources into security zones bounded by network perimeter controls that enforce mandated separation policies.
Security Zones are put in place to:
- Protection:
- A ‘Managed Boundary’ for all user access to applications and systems
- Implement granular role-based controls on traffic, users and assets
- Manage Inter-Zone communications
- Including between sub-zones
- Enforce policy and regulations
- Data confidentiality and integrity rules for data stored within a zone
- Detection:
- Monitor Inter-Zone communications
- Gain visibility of traffic, users and assets
- Logging and Event Correlation
- Elevate alerts for events using a SIEM/Analytics
- Prevent Inter-Zone data leakage using a DLP solution
- Containment:
- Control communications and resources on both inbound and outbound requests
- Set a default deny policy on all inter-segment connections
The key benefits of network segmentation and policy-based Zones are, as follows:
- Ability to Limit Exposure and Impacts
- Access Control: Firewall, VPN, Proxy
- Risk-Based Organization and Access
- Focus on Protecting Critical Assets
- Impossible to Protect Everything Equally
- Ability to Detect Suspicious Activity
- Visibility is Key (Sensors / Network Taps on Zone Gateways)
- IDS/IPS, Netflow, Packet Capture, Traffic Analysis, Analytics
- Network Behavior Anomaly Detection (NBAD)
- Predictive Threat Modeling
- Group Critical Assets and Users to Log and Monitor
- Visibility is Key (Sensors / Network Taps on Zone Gateways)
- Enable Containment of an Infection or Compromise
- Lockdown a Zone or Sub-Zone to prevent further impacts
- Expedite the Eradication and Recovery
- Investigate
- Incident Response
- Recovery (Backup and DR)
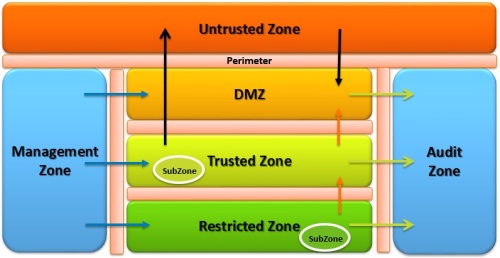
Layered Zone Components
The conceptual Adaptive Zone Defense design proposes 7 foundational layers or zones that are described as, the Untrusted Zone for assets not under the organizations control, Semi-Trusted (DMZ) Zone for assets that are externally shared (either publicly or to 3rd parties), Trusted Zone for internal systems, Restricted Zone for high risk and/or mission critical systems, a Management Zone for network services and management systems and, an Audit Zone to isolate and protect security logging and monitoring.
There is also the concept of a Sub-Zone that is basically a Zone within a Zone that enables special cases, such as regulatory mandated segmentation.
- Untrusted Zone –
- External Systems (not owned by organization)
- Internet, Public data classification
- External Systems (not owned by organization)
- Semi-Trusted (DMZ) –
- Externally-Exposed systems
- Public data classification
- 3rd Party Exposed systems
- Business Partner systems
- Externally-Exposed systems
- Trusted Zone –
- Internally-Exposed systems
- Internal data classification
- Confidential data classification
- Internally-Exposed systems
- Restricted Zone –
- High-Risk Mission Critical systems
- Restricted data classification
- High-Risk Mission Critical systems
- Management Zone –
- Network Management systems
- Virtualization Management
- Security Management systems
- Network Management systems
- Audit Zone –
- Regulatory Compliance
- Security Logging
- Security Monitoring (SIEM)
- Sub-Zones –
- Zones divided into Subzones
- Span Global Sites
- Special Cases
- Regulatory Mandated
- Zones divided into Subzones
High-Level Zone Design
The following graphic presents a conceptual high-level zone design that provides a foundation for a series of multi-layered zones based upon the device or systems Application Security Profile criteria. The criteria will be applied to this security model to develop the Application Security Design (Placement, Policy, Controls) based upon the Zone Architecture Rules as well as Application Architecture Taxonomy (discussed further in the next blog).
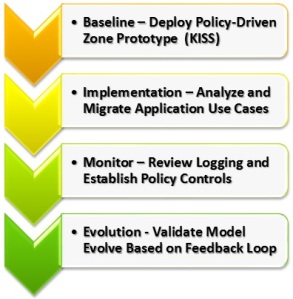
Zone Deployment and Migration
The critical success factor is in the Zone Deployment and Migration to move servers and systems to this model. This section provides an overview of the considerations and we will go into more detail in a future blog on this topic.
Zones – User Experience, Perception and Buy-in is key –
- Baseline Prototype
- Start Open/Simple
- Gain Quick Key Wins
- Implement / Migrate
- Analyze Application Use Cases
- Group by Service / Dependency
- Migrate to Zone Structure
- Analyze Application Use Cases
- Monitor
- Review Logs and Connections
- Establish Progressive Policy Controls
- Iterative Improvement
- Validate the Model with Feedback Loop
- Reverse Engineer Policy/Standards
- Structure as needed
- Iteratively Evolve over time
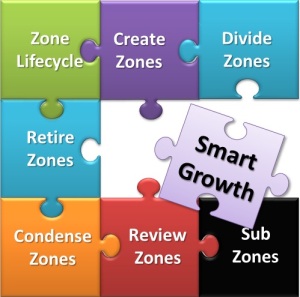
Zone Lifecycle Management – Smart Growth
Like Firewall Rules, Network Security Zones are organic and can easily become complex over time as new services and servers are deployed. It should be noted that the original Zone Architecture and Design was based upon the security model and business requirements at one point in time.
The concept of Adaptive Zone Defense talks to the critical need to continually review the Zone Design and to validate it against the needs of the business, new services, application and system deployments, new relationships, and so on.
Based upon assessments of 100’s of organizations the typical challenge with legacy DMZ approaches is that they start out well designed and organized. Over time the security model does not quite fit a new business need or deployment and/or the security model is not well understood and so either exceptions are made or human errors are made. The result is a DMZ implementation that is not only complex and harder to manage and maintain but also at risk of human error with configuration and implementation mistakes creating backdoors or side doors.
Keeper of the Zones – Security Vision
IT needs to be continually educated about the Zone Design, the business rules and the security model so that it is clearly understood. In addition, the Application Architecture Taxonomy (see below) needs to be integrated early in the cycle of service and server deployment processes and refreshes so that deployments are included in a risk assessment, are designed appropriately and thus, are placed within the Zone Design based upon both their connectivity and security needs to protect them and not break the model.
Zones need an owner, the keeper of the Zones and need to be managed to enable Smart Growth –
- Create Zones
- Based on Risk Assessment and Mitigation
- Application Profile – Placement
- Divide Zones
- Risk Profile Changes
- Special Cases, Security Exceptions
- SubZones
- Zones within a Zone
- Review Zones
- 6 Monthly Zone Organization Review
- Condense Zones
- Monitor and Consolidate
- Retire Zones
- Remove Zones from prior temporary Security Exceptions
- Remove Zones from prior temporary Security Exceptions
Conclusion
Security zone isolation is a lot of work, at least initially, but it offers a tangible Return on Security Investment (RoSI) that helps stop that bad end-user(s), a weak remote office(s), a malware infection or, a persistent attacker from compromising the whole network.
In Adaptive Zone Defense – Part 2 we develop a key profile that is currently termed an Application Architecture Taxonomy that considers Applications and their relationships as well as Users and their relationships. profile organizations and are currently in operation.
In future parts we will tie this all together in terms of how to profile applications based upon data classification and risk assessment as well as communications needs to determine the appropriate zone placement, protection controls and, access control policy. We will also discuss the deployment and migration considerations which are extremely critical to success. Lessons learned.
Thanks for your Interest!
Nige the Security Guy.