Adaptive Zone Defense – Part 2
January 7, 2014 9 Comments
Adaptive Zone Defense – Part 2
Adaptive Zone Defense – Part 1
Adaptive Zone Defense – Part 3
Adaptive Zone Defense – Part 4
Network segmentation is commonly used in network design to – increase network performance, create individually segmented networks to simplify network management, and divide networks up to create separate security zones. Because the APT is a “communicable disease” any part of a network involved with critical data can become infected.
By limiting and intelligently managing communications between services and systems it helps contain an infection or compromise to keep malware or a persistent threat from running rampant.
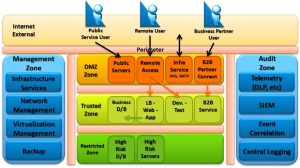
Adaptive Zone Design Template
In Adaptive Zone Defense – Part 1 we proposed a conceptual and high-level security zone design template (see graphic) that we will use as a foundation in this series and build upon with some detailed use cases and traffic flows in Part 3.
Conceptual Zone Design Template
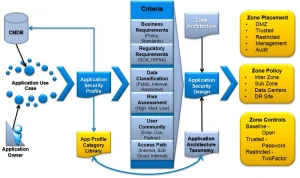
In part 2 we are going to first develop another foundation, known as Application Architecture Taxonomy that talks to application and system placement, organization and, management within the proposed zones.
Application Architecture Taxonomy
The goal of the Application Architecture Taxonomy is to identify the requirements, dependencies and profile criteria needed to determine the application and system zone policy, placement, and controls.
The Application Architecture Taxonomy provides a correlation of application flows as an overlay to the network architecture in order to understand how traffic is delivered from the various user communities to the servers supporting the applications.
It provides understanding of who is talking to what and what portions of the network are used to deliver the services as a set of Applications and their relationships together with Users and their relationships.
The information discovered in the application taxonomy phase will be used to profile Application Use Cases as they are migrated to:
- Define the types of data that exist and how best to establish risk classification (High, Medium, Low Risk) categories that meet the organizations business and risk requirements
- Determine the requirements around application and system zone placement as well as the applicable security policy and controls needed to ensure that the network is deployed with the appropriate security.
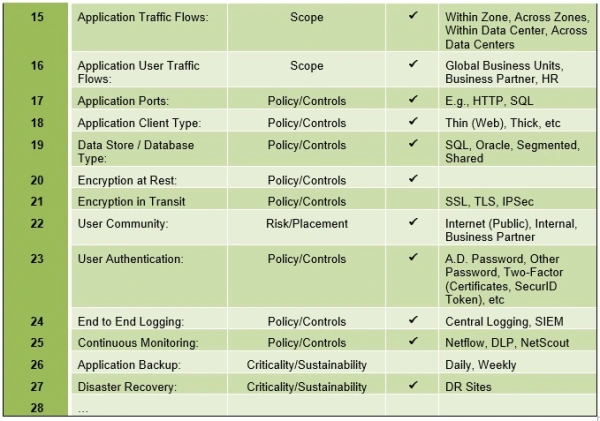
The following table presents a list of the criteria that are useful in profiling the application, to identify security requirements for risk assessment and, to determine system placement and protection.
Example Application Architecture Taxonomy Matrix
Security Control Solution Set
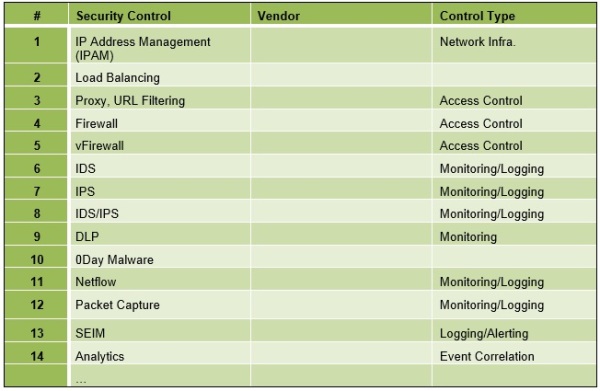
The Security Control Solution Set identifies the list of tools, technologies and, solutions that can be as options used to protect, log and, monitor applications and systems within the Zones and between Zones both physical and virtualized. An example table is illustrated below.
Example Security Control Solution Set
Risk Rating Controls Matrix
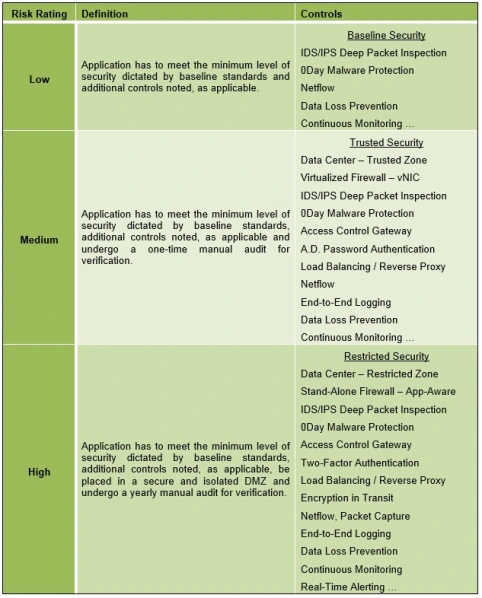
The Risk Rating Controls Matrix maps the risk, as determined by application or system criteria in terms of data classification, risk assessment and applicable law/regulation and/or policy to the minimum set of controls and restrictions that are required for the rating and/or zone placement.
Risk Rating Controls Matrix
Security Zones, Community & Controls
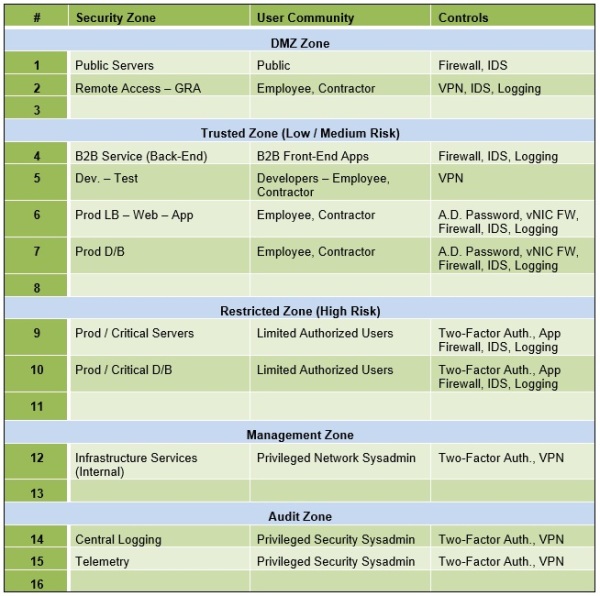
The Security Zones, Community and Controls worksheet enumerates all of the Security Zones and identifies the User Community (exposure) as well as applicable Controls that are applicable to manage the Zone Perimeter. This is a worksheet that is further developed and refined and maintained over time to describe and manage the design and current deployment.
Security Zones, Community and Controls Worksheet
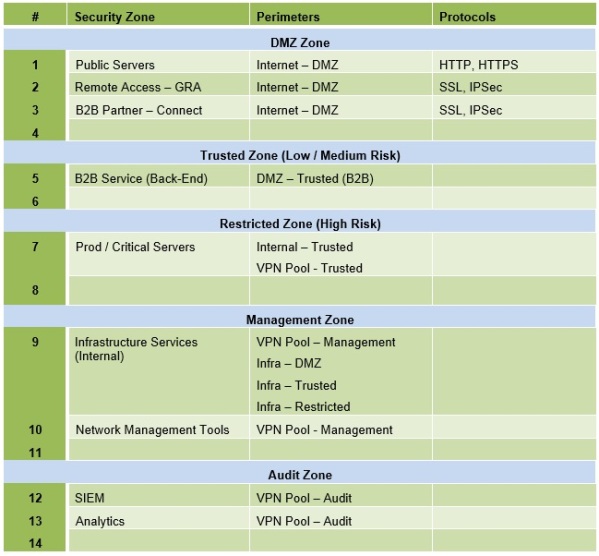
Security Zones, Perimeters & Protocols
The Security Zones, Perimeters, and Protocols worksheet is used to identify the connectivity between Zones across Perimeters and enumerates the allowed protocols between Zones as well as connection origination. This is a worksheet that is further developed and refined and maintained over time to describe the design and deployment.
Security Zones, Perimeters, & Protocols
Conclusion
This blog provides a key foundation to describe a set of tables and worksheets that can be used to document the criteria needed to profile applications and systems as well as manage their security posture in terms of Zones, perimeters, placement, protocols, policy, community and, controls.
The worksheets enable best-practice management and organization, to prevent DMZs or Zones that organically evolve over time and are no longer compliant with the original security design and posture. They enable the inventory, classification and organization of critical data and assets with a focus on mapping Applications and their relationships together with Users and their relationships across and within Zones.
In Adaptive Zone Defense – Part 3 we expand upon the conceptual and high-level security zone design with application architecture taxonomy that was introduced in Parts 1 and 2 to provide some practical use cases and more detailed examples of its implementation with traffic flows and inter-zone relationships.
We will also discuss application deployment integration, i.e., to ensure that this zone design and process is integrated into the greenfield deployment (or refresh) of applications and systems as well as a waiver process to manage temporary exceptions.
Coming Soon
In Adaptive Zone Defense – Part 4 we will tie everything together with the above taxonomy, tables and worksheets to describe the rationale and process flow from examining a new application or system, reviewing the data classification, risk assessment and, criteria and, identifying the placement, policy and controls.
References
This Adaptive Zone Defense – Part 2 blog is also a part of the APT Strategy Series and complements and builds upon the Adaptive Zone Defense – Part 1 and the Defensible Security Posture blogs.
Thanks for your interest!
Nige the Security Guy.


Pingback: Security Series Master Index | Nige the Security Guy
Pingback: Adaptive Zone Defense – Part 1 | Nige the Security Guy
Pingback: APT Strategy Series | Nige the Security Guy
Pingback: Adaptive Zone Defense – Part 3 | Nige the Security Guy
Pingback: APT Strategy Guide | Nige the Security Guy
Great article, however I do have a question.
On the Table for “Security Zones, Perimeters, & Protocols” You list the perimeter of the DMZ as the DMZ. Then continue to use the zone’s as borders for some, but not other’s. If you were to redraw that table, would you keep it the same, or illustrate it out with the firewalls in place between zones? “DMZ-Border Firewall”, “DMZ-Internal Firewall”, Prod Firewall, etc etc?
Yes … It was conceptual and oversimplified. There can be external facing DMZs and internal facing DMZs all gated by a Firewall. Need to review requirements and data flows, session initiation, containment etc
Pingback: Adaptive Zone Defense | ulyssesx86
Looking forward to part 4. Any thoughts around adding Micro-segmentation to tie it all together? Your sub zones can be come east-west traffic traffic control micro:segments to go along with high level zones/segments based on risk profile:dev/prod/compliance/etc. I think it would be great to talk about potential solutions such as SDN, NGFW to wrap it all together.