Advanced Threat Defense – Part 1
October 2, 2013 3 Comments
Advanced Threat Defense – Part 1
APT Strategy Series
Defensible Security Posture
APT Defense Puzzle
APT Risk Assessment
APT Incident Response
Adaptive Zone Defense
Many organizations continue to struggle to achieve network visibility into a number of advanced, targeted, and layered threats that evade detection by traditional approaches to incident management.
This APT Strategy Series blog offers readers a preview of a proposed foundation and strategy for Advanced Threat Defense. While there is no APT silver bullet there is much an organization can do with a well-designed and managed defensible posture to Protect, Detect, Contain, Eradicate and, Recover to minimize impact and cost.
Situational Awareness
Attackers are continuously evolving and becoming smarter, the largest looming threat to an organization is always that which it does not know or cannot detect. What is changing is that perpetrators understand that their victims can’t cover all their bases all the time. So DDoS attacks can be used as decoys to divert attention. This way, attackers can subsequently move to sectors that are more vulnerable.
But coming up with a standardized means of defending against these attacks presents a paradoxical challenge: while the ever-expanding risk footprints and evolving foes calls for more regulation in security, increased regulation effectively provides cybercriminals with a handbook on how to circumvent an organization’s security.
In an ideal world, every security manager would be able to assess their organization’s security ecosystem at any given time and be able articulate the current security posture. But for that to happen, risks must be known and acted upon with speed and intelligence, incoming events must be logged and scrutinized in real-time, and threats must be identified and anticipated before they become full-blown attacks.
Unfortunately, we do not live in an ideal world and we cannot obtain “situational awareness” and reap its benefits without the right security architecture, technology solutions and operational practices. Overall, it is imperative for organizations to integrate a well designed architectural blueprint with capable security technologies together with security intelligence and resource skills/expertise in order to achieve a more comprehensive threat perspective and informed risk management.
Recent Trends Increase Stakes
Business is about managing risk. Every business decision has inherent risk. It is essential to understand and make decisions based on the cost and benefit of that risk. CISOs no longer lay awake at night just worrying about defending their organization’s perimeters and the latest malware infection. The challenges facing security leaders today are far more complex and challenging.
The following are examples of recent trends with a significant impact on risk:
- BYOD
- Cloud
- Cyber Threats
- Mobility
- Social Media
It is time to rethink security in a broader holistic context and integrate across silos and functional roles so that organizations can protect what really matters: intellectual property and critical data. The challenge is to create an integrated ecosystem that is fully prepared to provide situational awareness visibility, detect any anomaly, investigate it to verify and, remove threats in a defensible posture.
Traditional technologies are still needed to catch vulnerability-based attacks, these technologies need to be layered to enable the organization to detect, monitor and stop an attack at each stage of the kill chain. Our goals are to:
- Evaluate and Manage Threat/Risk
- Establish Defensible Security Posture
- Develop Skills and Expertise
- Defend against Advanced Threats
- Improve Detection and Reaction time
- Manage Operational Costs
Distributed Defense Ecosystem
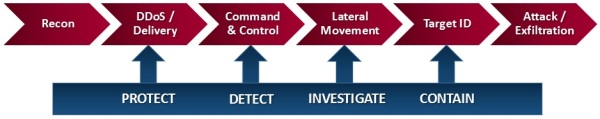
The goal in a Distributed Defense Ecosystem is to align detection and mitigation technologies with earlier phases of the intrusion kill chain (see: Defensible Security Posture) to stop persistent threats. Defensive measures at each stage of the kill chain help ensure resiliency, particularly when faced with adapting threats. When one defense fails to stop or detect an attack, hopefully one of the others will succeed. This is the modern approach to defense in depth – intelligence-driven detection and mitigation aligned with the intrusion kill chain.
- Layer 1: Protect – Defensible Architecture Foundation
- Identity and Role-Based Access (Who)
- Asset Inventory Classification (What)
- Application & System Zoning/Controls
- Application Connectivity Management
- Activity Logging and Monitoring
- Instrumentation and Telemetry
- Data Collection and Mining
- Layer 2: Detect – Security Operations
- Calibration & Validation
- Threat Intelligence/Indicators
- Situational Awareness
- Behavior Baseline
- Anomaly Detection
- Attack Patterns
- Layer 3: Contain – Incident Response
- Anomaly Verification
- Damage Assessment/Containment
- Incident Response
- Layer 4: Investigate – Lessons Learned
- Root Cause Analysis
- Break the Kill Chain
- Remediate and Recovery
In Advanced Threat Defense – Part 2 we will further develop this initial foundation and strategy to discuss the various defense-in-depth, situational awareness, containment and, response layers in more detail to begin to define the framework, technology and, practices for a Defensible Security Posture.
Conclusion
Dealing with advanced attackers is not for immature security organizations. Organizations need to master security fundamentals and have good security practices in place. Our Security Architecture Series (see links below) takes readers Back to Basics to assemble and align the pieces necessary to develop, update, or validate a modular and flexible security architecture that forms the basis for Advanced Threat Defense.
As discussed in our Threat & Vulnerability Management blog, organizations need to have already hardened key devices and implemented a strong device hygiene (patch and configuration management) program. It is also necessary to properly segment the network to make it difficult for attackers to get at important data, which will be discussed more fully in the Application & System Zoning blog (aka Adaptive Zone Defense) and Service Communication Management (aka Application Architecture Taxonomy) blog which profiles applications based on classification and risk, determines zone placement and, defines policy and controls.
While traditional endpoint protection is not ‘the’ sole solution organizations do still need some level of protection on key devices with access to sensitive data.
To help improve security posture, penetration testing and security validation testing is key. There is a lot to be learned from these tests, (also see: Vulnerability Assessment Remediation) regardless of whether they are required or not. The penetration testing exercise can be used to validate security operations / monitoring visibility and detection as a real-world attack scenario, as well as a training tool for the forensic team to provide lessons learned regarding overall security issues.
Security Architecture Series
- Think You’re Secure? Think Again.
- Security Architecture Primer
- Security Architecture Baseline
- Risk-Aware Security Architecture
- Develop Security Architecture
- Product and Solution Selection
- Security Architecture Implementation
- Adaptive Security Lifecycle
- Architecture Case Study – Part 1
- Architecture Case Study – Part 2
Thanks for your interest!
Nige the Security Guy.



Pingback: APT Defense Puzzle | Nige the Security Guy
Pingback: Security Series Master Index | Nige the Security Guy
Pingback: APT Strategy Series | Nige the Security Guy