Security Series Master Index
May 30, 2013 3 Comments
Security Series Master Index
This blog will be maintained to provide a Security Series Master Index summary of all of the blogs to assist in site exploration and navigation – as well as preview upcoming blogs.
The currently planned series are, as follows:
- Security Architecture Series
- APT Strategy Series
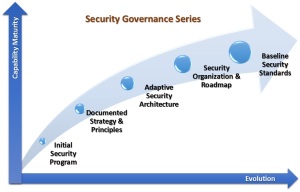
- Security Governance Series
- Risk Management Series
- Security Assessment Series
- Miscellaneous Topics
Security Architecture Series
The Security Architecture Series build upon each other and contains:
- Think You’re Secure? Think Again.
- Security Architecture Primer
- Security Architecture Baseline
- Risk-Aware Security Architecture
- Develop Security Architecture
- Product and Solution Selection
- Security Architecture Implementation
- Adaptive Security Lifecycle
- Architecture Case Study – Part 1
- Architecture Case Study – Part 2
APT Defense Strategy Series
The APT Strategy Series contains, as follows:
- APT Strategy Series
- An introduction to the APT Strategy Series together with the rationale behind the need for a well-designed Secure Architecture and Design foundation
- Defensible Security Posture
- The basic idea of a Defensible Security Posture is that you aren’t striving for an absolute, but rather for a position (or posture) that is able to be defended even when it’s infiltrated
- Defensible Security Posture – Part 2
- How can you leverage the Defensible Actions Matrix? A defensible actions matrix defines processes and procedures that can impact an attacker’s capability at various stages of the cyber kill chain.
- Advanced Threat Defense – Part 1
- Focuses on top-down Architecture & Strategy to address Advanced Threats with ability and visibility to Detect and Contain
- APT Defense Puzzle
- Focuses on bottom-up Actionable Security Posture Improvements: Checks, Practices, Controls, Indicators
- APT Detection Framework
- In order to begin to understand and to be able to defend against targeted attacks a detection matrix is needed for visibility, analysis and, to ensure that all threat scenarios are considered with no gaps in defense
- APT Detection Framework – Part 2
- There is a trend underway in the information security field to shift from a prevention mentality — in which organizations try to make the perimeter impenetrable and avoid breaches — to a focus on rapid detection, where they can quickly identify, contain and mitigate threats.
- APT Detection Indicators – Part 1
- In a world where organizations need to be watching or monitoring their networks continuously knowing what to look out for is critical
- APT Detection Indicators – Part 2
- Advanced Persistent Threats (APT) typically exhibit recognizable attributes and patterns that can be monitored by readily available, open source tools
- Adaptive Zone Defense – Part 1
- Limiting and intelligently managing communications between services and systems on an organizations network helps contain an infection or compromise to keep malware or a persistent threat from running rampant
- Adaptive Zone Defense – Part 2
- In Adaptive Zone Defense – Part 2 we develop another key foundation, known as Application Architecture Taxonomy that talks to application and system placement, organization and, management within the proposed zones.
- APT Red Teams – Part 1
- How do you prevent an APT? Red Teams enable continuous improvement and optimization from counter-intuitive sources to help mitigate advanced threats
- APT Red Teams – Part 2
- Addressing security more aggressively and working to identify areas of weakness is a more sensible, and ultimately, more effective approach than working to build a “bigger wall” that you hope attackers can’t get through
- APT Response Strategy – Part 1
- How do you implement a Plan C? Organizations are starting to recognize the ever increasing importance of rapid and well orchestrated incident response capabilities as a key component in their defense-in-depth strategy.
- APT Response Strategy – Part 2
- [Coming Soon]
- APT Threat Analytics – Part 1
- How can you predict emerging threats? Threat intelligence and analytics continues to dominate the headlines and attention of organizations seeking viable options in their escalating battle against advanced threat actors.
- APT Threat Analytics – Part 2
- With the increase in advanced, multidimensional threats, more and more organizations are considering development of an in-house threat intelligence program
- APT Operational Maturity – Part 1 [Coming Soon]
- How can you evolve towards effective Visible Security Operations? An update to my 90’s Security Maturity Model based on recent sophisticated threats and determined attackers.
- APT Intelligent Operations – Part 1 [Coming Soon]
- How can you build an Intelligence-Driven Security Operations platform using commercial and/or open-source tools.
Security Governance Series
The Security Governance Series contains, as follows:
- Security Program Best-Practices – Part 1
- Security Program Best-Practices – Part 2
- Security Program Best-Practices – Part 3
- Security Program Best-Practices – Part 4
- Security Program Best-Practices – Part 5
- Risk Management Strategy [Coming Soon]
- Data & System Classification [Coming Soon]
- Identity Management & Role-Based Access [Coming Soon]
- Next-Generation Intrusion Prevention (IDPS) Strategy [Coming Soon]
- More to follow
Security Assessment Series
The Security Assessment Series contains:
- Common Compliance Framework [Coming Soon]
- Vulnerability Assessment Remediation
- Threat and Vulnerability Management
- APT Threat Assessment
- Penetration Testing and Security Validation [Coming Soon]
- Risk Assessment and Roadmap
- ISO 27002 Security Benchmark
- Security Health Check
Thanks for your interest!
Nige the Security Guy.



Nice work. 🙂 Keep it up. I’ll ensure that even I contribute in your endeavour
Please do contribute and I will credit you as author and promote.
Nige.
Pingback: Adaptive Zone Defense – Part 1 | Nige the Security Guy